Server hack affects 45 USU webpages
Utah State University servers were hacked Friday night by what is believed to be a professional hacker group called “AnonGhost.” According to USU IT, the hack only lasted about 45 minutes, and all affected webpages are now operational.
“We had a pretty good response,” said Regan Zane, professor of electrical and computer engineering, whose department was among the hacked webpages. “We recognized almost immediately when we were hacked.”
USU IT security team member Miles Johnson said only webpages were affected, and the university’s underlying operating system was left intact. USU IT is still trying to understand how the server was compromised.
There were approximately 45 websites which had the default index page replaced with a propaganda index file. The sites for Aggie Radio and the American Anthropological Association Children and Childhood Interest Group were deleted, but were backed up and have since been restored. The university’s Power Electronics Lab (UPEL) site was completely subverted.
“It’s always something you worry about (because) it happens all the time,” said Kevin Kennedy, a student who manages the UPEL webpage. “It’s a known problem with it, and we installed the update. That’s really the only thing we can do. There’s no way to completely guard against it.”
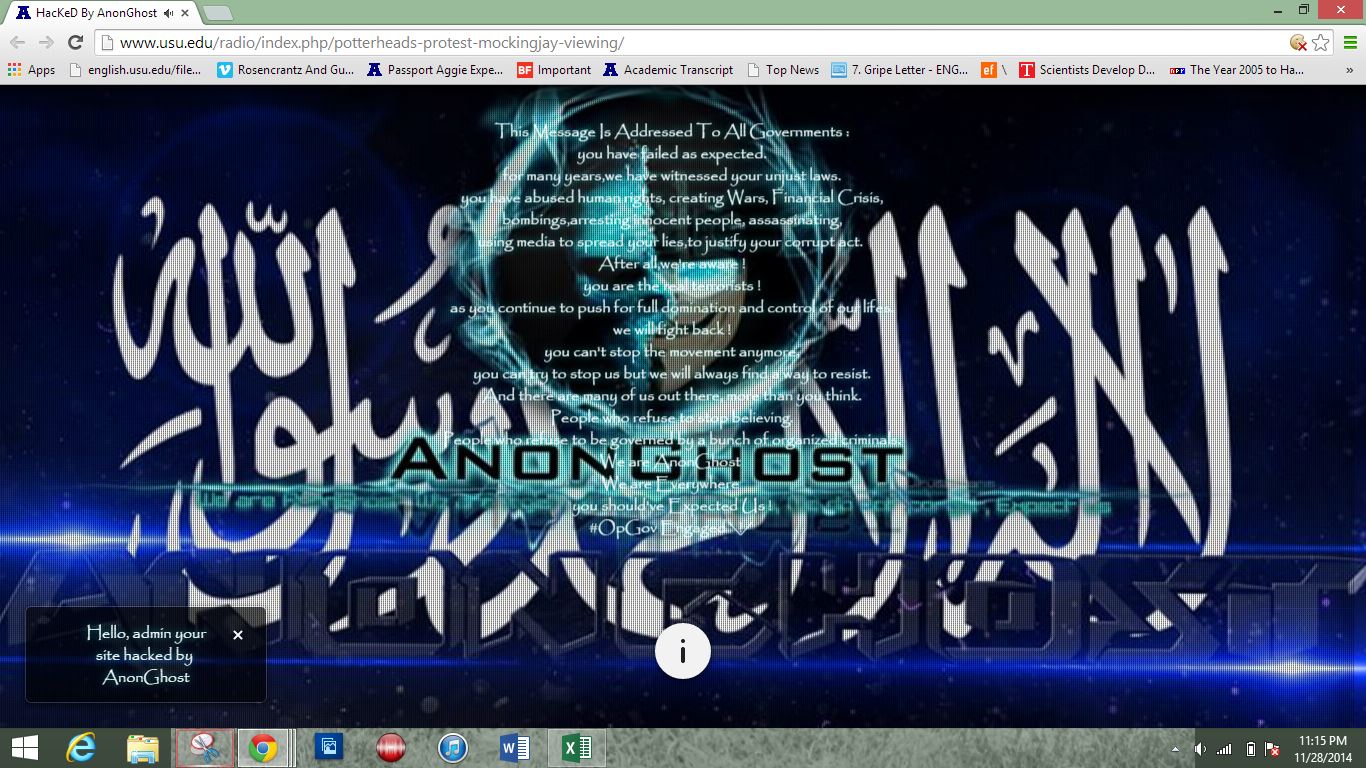
The affected servers were defaced with ISIS propaganda and a message, which was addressed “To All Governments.” The message said that governments are failing to uphold human rights and called government officials “organized criminals.”
A male voice recited the Qu’ran, speaking in the classical, or Koranic, standard dialect. Background images of the websites included ISIS flags and symbols as well as the group’s signature skull graphic.
Although the message did not make any specific threat, it was aggressively anti-Semetic. It also read, “As you continue to push for full domination and control of our lives, we will fight back.”
The message ended with #OpGovEngaged. At the bottom of the page, an icon was linked to the hacker group’s Twitter page, @AnonGhostTeam.
Johnson said there’s not much they can tell about the organization from the hack.
“We need to look at their actions,” he said. “What they say can be misleading, so we need to look at what their actions are accomplishing.”
Johnson said the hack’s characteristics are typical of hostile governments.
“Their tools are well-refined and polished,” he said.
Johnson estimates the group has been together for two or three years, but it could be as much as 10.
Washington University and Columbia University were hacked last week by the same group. Washington’s affected websites are currently disabled, but Columbia’s have been restored.
“The way to avoid this in the future is to more aggressively monitor our content,” Johnson said. “We have that monitoring for the main campus website, but it’s sites run by individuals — students, faculty, researchers — that are being targeted. … This is going to keep happening as long as we are a research institution.”
USU IT will be monitoring university webpages more closely, and better measures can be taken to prevent security breaches as they learn how the hacker accessed the system.
—brennakelly818@gmail.com